Meraki is the first and only solution that provides device based security policies, built-in NAC, and built-in mobile device management. Meraki includes everything you need for a secure, reliable, headache-free BYOD network — 100% integrated, without added cost or complexity.
The number of user-owned devices has grown at an unprecedented pace in recent years, with new iPads, Androids, and smartphones connecting every day. This has become a new and often very frustrating problems for administrators to deal with. While there is a clear need for access for these devices, security and administration of these devices becomes a serious concern. It’s imperative to keep network access secure and apply device-specific policies without opening security holes or causing an undue support burden.
Built-in BYOD Support
With built-in BYOD (Bring Your Own Device) support, Meraki makes it easier than ever to securely support user-owned iPads, tablets, smartphones, and laptops – without extra appliances, licenses, or complex VLAN configurations.
Automatically Identify Devices Connected to Your Network
Integrated Layer 7 client fingerprinting technology lets you see all the iPads, iPhones, and Android devices on your network, with no configuration required. Client devices are automatically identified and classified, letting you distinguish between iPads and iPhones, device operating systems, and even manufacturer.
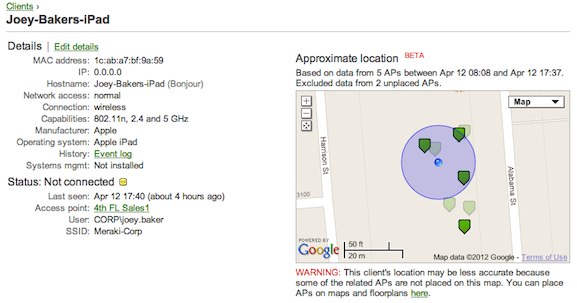 | |||||||||||||||||||
Meraki's Systems Manager provides web based centralized management, diagnostics, and monitoring for all mobile devices managed by your organization. Systems Manager monitors all devices, showing useful metrics including client hardware/software information and recent location, and even lets administrators remotely lock and erase devices.
Automatically apply policies by device type
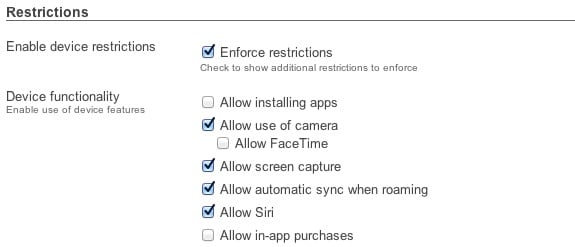
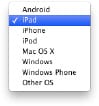 Device-specific policies can be automatically applied to restrict, quarantine, or throttle user-owned devices.
Device-specific policies can be automatically applied to restrict, quarantine, or throttle user-owned devices.Meraki’s client fingerprinting technology immediately recognizes iOS, Android, Windows, and Mac devices, and even lets you apply more restrictive policies for unknown devices.
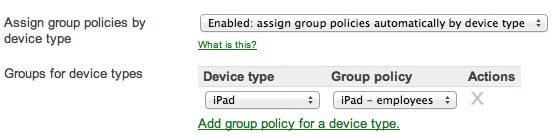
Isolate your network from user-owned devices or integrate them securely using additional, automatically applied device-specific policies. Configuration takes just two clicks.

Protection against viruses and malware
Integrated network access control (NAC) prevents unmanaged devices
from spreading viruses and malware on the network. All commonly affected devices are
scanned, ensuring antivirus software is installed and running.
Clients that fail to meet security requirements are placed in a quarantine, where antivirus software can be downloaded.
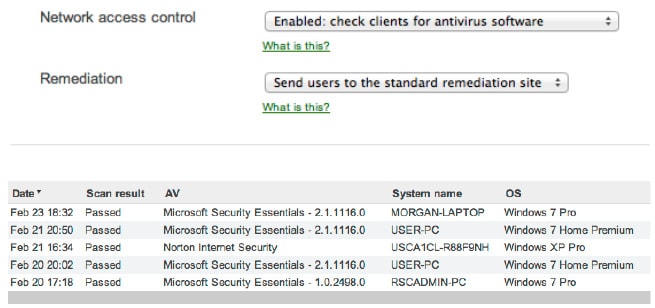
Clients that fail to meet security requirements are placed in a quarantine, where antivirus software can be downloaded.

Analyze all device activity activity with automatic reporting
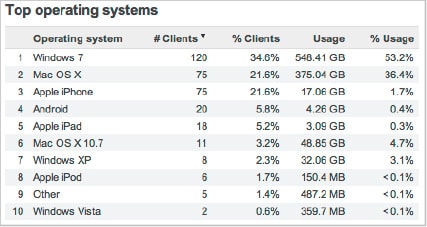 See how many devices are connected, measure the bandwidth
they’ve used, and even see their percentage of total traffic.
See how many devices are connected, measure the bandwidth
they’ve used, and even see their percentage of total traffic.Network summary reports are delivered to your inbox at any time or on an automatic, monthly schedule.



No comments:
Post a Comment